Thank you for inviting the Federal Trade Commission to participate in the Department of Justice's Elder Justice Initiative federal webinar series. My name is Lisa Schiffer Lee and I'm an attorney in the FTC's Division of Consumer and Business Education. In this webinar, we will discuss scams and identity theft affecting older adults. Whether you're an older adult yourself or someone who works with older adults, we will provide tips for you. The webinar will be divided into two parts. First, we'll discuss scams and look at the latest trends, tips, and tools. We'll focus on the FTC's "Pass It On" campaign, which is designed to get older adults talking about scams and sharing knowledge to prevent others from falling victim. For those working with older adults, "Pass It On" is a great tool to use at scam jams or presentations in the community. In the second part, we'll discuss identity theft trends, tips, and tools. We will focus on IdentityTheft.gov, the federal government's one-stop resource for reporting identity theft and getting detailed advice on fixing problems caused by identity theft. Let's start with scams. What trends are we seeing? The FTC's 2016 complaint data shows that imposter scams are the second largest complaint, followed by identity theft as the third largest. So, in this presentation, we will mainly focus on these two areas - imposter scams and identity theft. When it comes to scams, how are scammers contacting consumers? As shown in the pie charts, the vast majority of scammers are reaching out by phone, accounting for 77% of contacts in 2016. Email contacts make up 8%, and contacts through the internet account for 6%. While online scams are a concern, it's important to recognize that most scams are still happening through phone calls. This information can be helpful for law enforcement and...
Award-winning PDF software





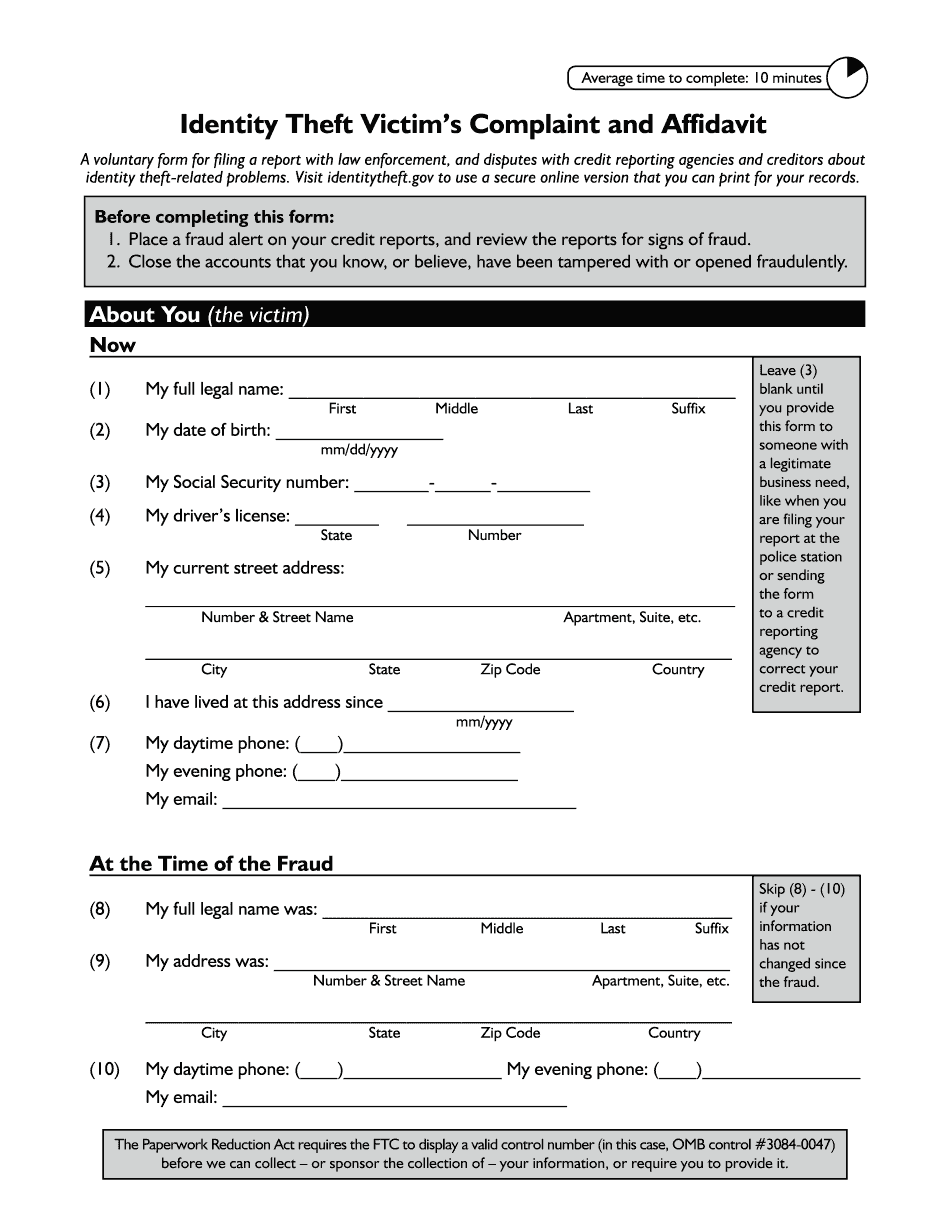
Ftc Id Theft Affidavit Pdf Form: What You Should Know
ID Theft Affidavit for detailed instructions. Privacy Violations in the United States March 4, 2025 — An anonymous submission submitted to our public access portal of over 5,000 Federal Government employees and contractors who had done work for a contractor involved with a violation of Privacy Act laws. Please use the form, Privacy Violations in the United States, to submit your own information. US-OEM Privacy and Security Policy Changes — October 22, 2013, The United States Department of Defense now has established a Federal Information Security Oversight Office to oversee the Department's information security processes and procedures. For years many US Government agencies have been plagued with outdated and incorrect security regulations, policies and processes. This report is your guide to compliance standards, requirements and best practices that were published on 12 August 2017. What is a “Best Practice”? — US Department of Homeland Security A Best Practice outlines a process for following when creating an Information Security Program. US Department of Homeland Security, Office of Information & Critical Infrastructure Protection Guidance for Information Security Policy, Implementation and Standards US Department of Homeland Security, Information Security Directorate, Identity and Access Management Center US Department of Homeland Security, Office of Information and Critical Infrastructure Protection, Guidance for Identifying, Managing and Storing Data of High Value to the Nation — April 29, 2018, Identifying, Managing and Storing Data of High Value to the Nation: Recommendations for the United States Government on Automated Identity Theft Detection, Retrieval, and Resolution Programs. Identification and Access Management Center — Guidance on Automated Authentication, Data Integrity, and Access Control — September 2016 The US Government provides a set of best practices to help mitigate or preempt the risk of Identity Theft. These guidelines provide a starting point for the Federal Government and industry who are working to meet the challenges of increasing information security, protecting sensitive and protected data, and safeguarding confidential business information. Guidance for Automated Identification, Data Integrity, and Access Control in the Department of Defense for Secure Data Automation The Government of Canada is working to ensure that the Canadian government is providing adequate protections for the private information of its citizens. To ensure that public services in the public interest are provided to Canadians, the Government of Canada must have the ability to collect, secure, protect and use the personal information of Canadians to protect the public interest.
online solutions help you to manage your record administration along with raise the efficiency of the workflows. Stick to the fast guide to do Ftc Identity Theft Victim's Complaint And Affidavit, steer clear of blunders along with furnish it in a timely manner:
How to complete any Ftc Identity Theft Victim's Complaint And Affidavit online: - On the site with all the document, click on Begin immediately along with complete for the editor.
- Use your indications to submit established track record areas.
- Add your own info and speak to data.
- Make sure that you enter correct details and numbers throughout suitable areas.
- Very carefully confirm the content of the form as well as grammar along with punctuational.
- Navigate to Support area when you have questions or perhaps handle our assistance team.
- Place an electronic digital unique in your Ftc Identity Theft Victim's Complaint And Affidavit by using Sign Device.
- After the form is fully gone, media Completed.
- Deliver the particular prepared document by way of electronic mail or facsimile, art print it out or perhaps reduce the gadget.
PDF editor permits you to help make changes to your Ftc Identity Theft Victim's Complaint And Affidavit from the internet connected gadget, personalize it based on your requirements, indicator this in electronic format and also disperse differently.
Video instructions and help with filling out and completing Ftc Id Theft Affidavit PDF