Lori Sis it a novice when it comes to doing business online due to your shopping mm-hmm banking banking everything sales are here the executive assistant had followed all the internet security rules and thought her transactions were safe until she tried to buy something with her bank card they told me it was declined and I was quite shocked about that the swent straight to her bank three thousand dollars was gone he pulled up my account on the screen he said I hate to tell you but you are the next victim of identity theft this advanced form of identity theft is called phishing where cybercriminals lure you into letting them into your computer to fish for sensitive information and the fishes have caught plenty as they cast an ever wider net in the last year attacks are up for a thousand percent costing consumers up to one and a half billion dollars you've probably seen the most common phishing attack an email like this usually urging you to reconfirm your account information don't click on that link it will take you to a bogus internet site that looks like the real thing they're so sophisticated that even computer security experts sometimes have a hard time telling the real ones from the fake ones once you type in your password you've opened your account to the cyber thief many believed to be connected to organized crime but Lori salways deletes those pesky email so how did they do it it's all happening invisibly in the background internet security expert Mike wider think smay have been hooked by a new kind of fishing called keyboard spyware that sneaky software hidden inside emails or programs that you download from the web the spyware then watches every keystroke you make keystroke...
Award-winning PDF software





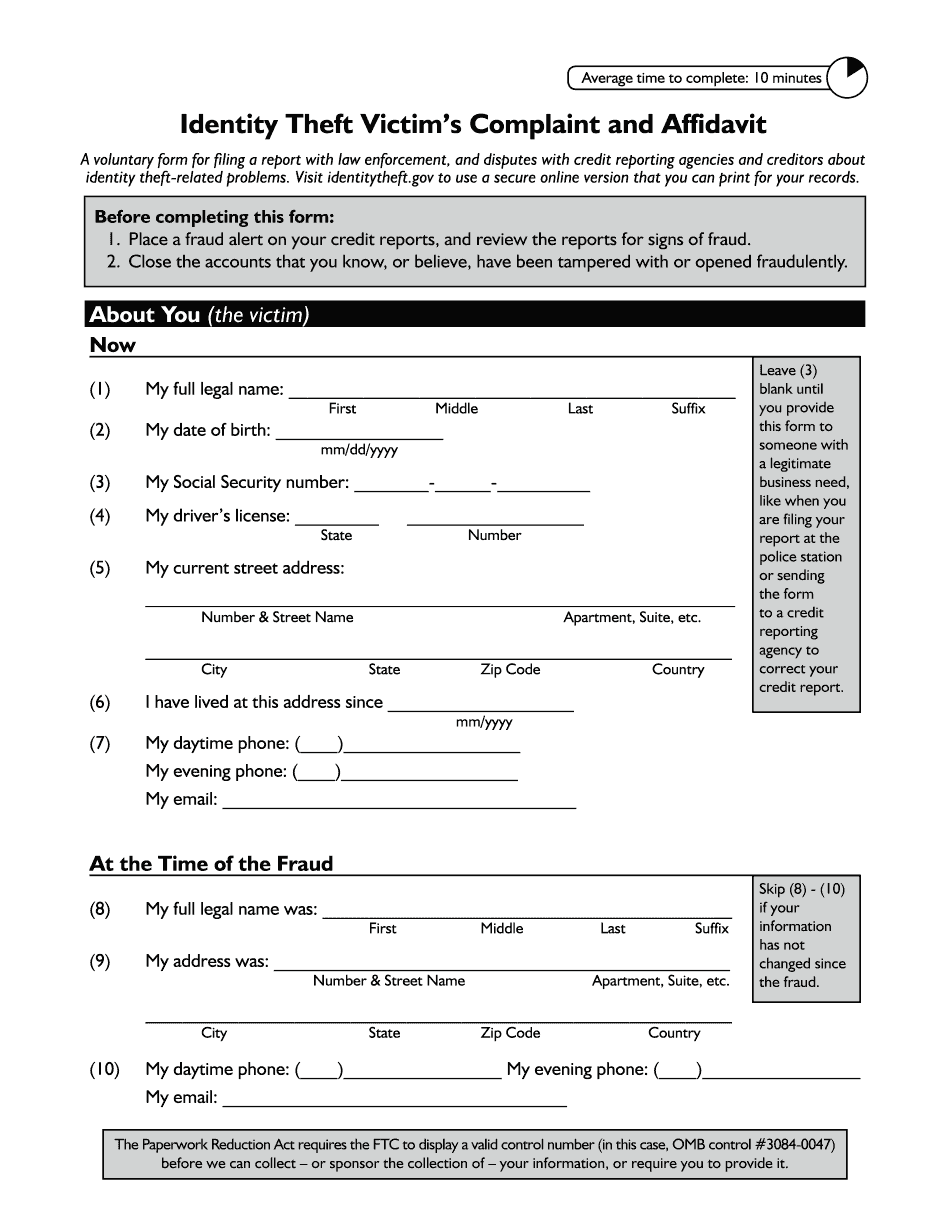
Identity theft recovery services Form: What You Should Know
How to Report Identity Theft — IRS If you've been the victim of identity theft or found your personal information exposed online, the IRS will work with you to identify the thief. Who Can Request An Identity Theft Report — IRS In some situations, you cannot report identity theft to the IRS. You may not have the ability to provide all the information needed for the identity theft investigation. You can work with us to find the right solution for you. Report Identity Theft Without A Request In some cases you may not be able to report your identification to the IRS. For example: • You cannot recover the stolen taxpayer information from your online account as it is not attached to your online taxpayer account. • You do not have access to the IRS's tax system. You should make arrangements with the IRS's call center to obtain information about how to make the online account available again. • The identity theft was committed using an Internet account, but the thief used a mobile device, desktop computer, or other device to obtain your taxpayer information. • The identity theft is related to fraudulent conduct. For example, you've already reported your identity stolen and are concerned that your financial information is at risk. If you are facing a fraudulent tax claim, you have three options: • Send an Identity Theft Report to the IRS. To report a new IRS Identity Theft, please report the information above and use the Identity Theft Report link. Report Identity Theft To Someone Else You can report identity theft information online by filling out a Form 5329, Identity Theft Affidavit. This form also may be filled out using the IRS-ID Theft Report Form at the bottom of this website page. Online Tax Filing System The IRS Identity Theft page has additional ways to report this type of incident. Who Can Report Identity Theft — IRS If you have been the victim of identity theft and would like the agency to look into your case, you may file a Form 4469, Report of Identity Theft, which is provided by the IRS. You may also request an Identity Theft Report online at IRS.gov. If this incident involves money or the use of another taxpayer's personal information, you can file a Uniform Fraudulent Claims Act Report (UFA HR) Form. You must file an IRS Form 4500-X (formerly 4469) within seven days of the first unauthorized use of your information. The information you provide in the application must be true and complete. File a UFA HR form with the other IRS account or filing for the same taxpayer.
online solutions help you to manage your record administration along with raise the efficiency of the workflows. Stick to the fast guide to do Ftc Identity Theft Victim's Complaint And Affidavit, steer clear of blunders along with furnish it in a timely manner:
How to complete any Ftc Identity Theft Victim's Complaint And Affidavit online: - On the site with all the document, click on Begin immediately along with complete for the editor.
- Use your indications to submit established track record areas.
- Add your own info and speak to data.
- Make sure that you enter correct details and numbers throughout suitable areas.
- Very carefully confirm the content of the form as well as grammar along with punctuational.
- Navigate to Support area when you have questions or perhaps handle our assistance team.
- Place an electronic digital unique in your Ftc Identity Theft Victim's Complaint And Affidavit by using Sign Device.
- After the form is fully gone, media Completed.
- Deliver the particular prepared document by way of electronic mail or facsimile, art print it out or perhaps reduce the gadget.
PDF editor permits you to help make changes to your Ftc Identity Theft Victim's Complaint And Affidavit from the internet connected gadget, personalize it based on your requirements, indicator this in electronic format and also disperse differently.
Video instructions and help with filling out and completing Identity theft recovery services